Data Center Physical Security
Deploy on an infrastructure protected by more than top experts in information, application, and network security. With Our Data Center Platform your applications and data take advantage of the same pervasive security model. MulakiHost data centers feature a layered model, including safeguards like custom-designed electronic access cards, alarms, vehicle access barriers, perimeter fencing, metal detectors, and biometrics. The data center floor features laser beam intrusion detection. Our data centers are monitored 24/7 by high-resolution interior and exterior cameras that can detect and track intruders. Access logs, activity records, and camera footage are reviewed in case an incident occurs. Data centers are also routinely patrolled by experienced security guards who have undergone rigorous background checks and training. Fewer than one percent of Mulakihost employes will ever set foot in one of our data centers.

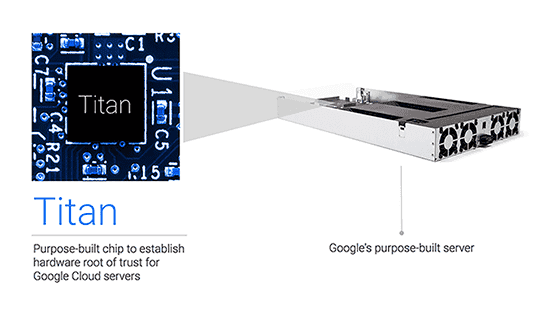
Trusted Server Boot
The only way to protect the boot process of a server is to secure it with an entity that can be trusted to always behave in an expected manner. We use same technology that is built for security by Google security chip called Titan to provide this root of trust. Titan enables the verification of the system firmware and software components, and establishes a strong, hardware-rooted system identity.
Data Disposal
When retired from Mulakihost’s systems, hard disks containing customer information are subjected to a data destruction process before leaving Mulakihost’s premises. First, disks are logically wiped by authorized individuals using a process approved by the Mulakihost Security Team. Then, another authorized individual performs a second inspection to confirm that the disk has been successfully wiped. These erase results are logged by the drive’s serial number for tracking. Finally, the erased drive is released to inventory for reuse and redeployment. If the drive cannot be erased due to hardware failure, it is securely stored until it can be physically destroyed. Each facility is audited on a weekly basis to monitor compliance with the disk erase policy.
Data Encryption
All data are encrypted for each account using more then one encryption mechanisms. The same encryption and key management policies, cryptographic libraries, and root of trust used for your data in MulakiHost are used by many of Mulaki Host production services, including Web Hosting, Server, Storage, MulakiHost own corporate data. Encryption is automatic, and no customer action is required. One or more encryption mechanisms are used. For example, any new data stored in persistent disks is encrypted under the 256-bit Advanced Encryption Standard (AES-256), and each encryption key is itself encrypted with a regularly rotated set of master keys.